Information Security
At Evotix, we understand our customers’ requirement to protect information we store on their behalf. To comply with this requirement, we employ several technical and organisational measures to ensure the in-transit safety and security of customer information, as well as confidence that information can be retrieved if presented with a ‘catastrophic event’.
We also make sure that access to customer information by staff is restricted – this means only certain departments and authorized people can access customer information and only for defined processes and procedures (for example, customer support, technical support and certain development tasks). All access to data is based on Principle of Least Privilege (PoLP) and directly linked to their need for access in line with their designated roles assigned within our HR management system. Each member of staff will use this data guided by their training, aligned policy, and ingrained process arrangements in accordance with the regulations of the General Data Protection Regulations and relevant legislation.
We maintain a robust Service Level Agreement to support customers for events from the routine to the extraordinary. As ICO registered data controllers with a voluntarily appointed DPO, we have designed and implemented a holistic information security regimen. This is guided by the GDPR articles and best practice legal and technical advice to enshrine policy, process, and practice into our wider management arrangement to ensure compliance, transparency and accountability that reports into the highest levels of management.
Several of our strategies to ensure data protection and integrity are shown below.
Our Provider
We use Amazon Web Services as our hosting provider. AWS is an effective Tier 1 provider, with a full list of protocols in place for data security and protection, including:
- Cyber Essentials Plus
- G-Cloud Approved
- SOC 1/SSAE 16/ISAE 3402 (formerly SAS 70)
- SOC 2
- SOC 3
- FISMA
- FedRAMP
- DOD SRG Levels 2 and 4
- PCI DSS Level 1
- EU Model Clauses
- ISO 9001 / ISO 27001 / ISO 27017 / ISO 27018
- ITAR
- IRAP
- FIPS 140-2
- MLPS Level 3
- MTCS
Full details available at: https://aws.amazon.com/compliance/data-center/controls/
Security
Our provider implements several security layers to protect customer information:
Physical Security
Physical Security includes locking down and logging all physical access to our data center .
AWS’ data centers are state of the art, utilizing innovative architectural and engineering approaches. AWS has many years of experience in designing, constructing, and operating large-scale data centers. This experience has been applied to the AWS platform and infrastructure. AWS data centers are housed in nondescript facilities. Physical access is strictly controlled at the perimeter and at building ingress points by professional security staff utilizing video surveillance, intrusion detection systems, and other electronic means. Authorized staff must pass two-factor authentication a minimum of two times to access data center floors. All visitors and contractors are required to present identification and are signed in and continually escorted by authorized staff.
AWS only provides data center access and information to employees and contractors who have a legitimate business need for such privileges. When an employee no longer has a business need for these privileges, his or her access is immediately revoked, even if they continue to be an employee of Amazon or Amazon Web Services. All physical access to data centers by AWS employees is logged and audited routinely.
Operations Security
Operational Security involves creating business processes and policies that follow security best practices to limit access to confidential information and maintain tight security over time.
- ISO 27001 based policies reviewed annually
- Documented infrastructure change-management procedures
- Secure document and media destruction
- Incident management function
- Business continuity plan focused on availability of infrastructure
- Independent reviews performed by third-parties
- Continuous monitoring and improvement of security program
Network Infrastructure
Network Infrastructure provides the availability guarantees backed by aggressive SLAs.
- High-performance bandwidth provided by multiple network providers
- Elimination of single points of failure throughout shared network infrastructure
- Cables properly trunked and secured
- Proactive network management methodology monitors network route efficiency
- Real-time topology and configuration improvements to adjust for anomalies
- Network uptime backed by Service Level Agreements
- Network management performed by only authorized personnel
Environmental Controls
Environmental Controls implemented to help mitigate against the risk of service interruption caused by fires, floods, and other forms of natural disasters.
The data center electrical power systems are designed to be fully redundant and maintainable without impact to operations, 24 hours a day, seven days a week. Uninterruptible Power Supply (UPS) units provide back-up power in the event of an electrical failure for critical and essential loads in the facility. Data centers use generators to provide back-up power for the entire facility.
Human Resources
Human Resources provides AWS employees with an education curriculum to help ensure that they understand their roles and responsibilities related to information security.
AWS only provides data center access and information to employees and contractors who have a legitimate business need for such privileges. When an employee no longer has a business need for these privileges, their access is immediately revoked, even if they continue to be an employee of Amazon or Amazon Web Services. All physical access to data centers by AWS employees is logged and audited routinely.
Security Organisation
Security Organisation includes, establishing a global security services team tasked with managing operational risk by executing an information management framework based on the ISO 27001 standard.
- Security management responsibilities assigned to Global Security Services
- Information Security Manager oversight of Security Operations and Governance, Risk, and Compliance activities
- Direct involvement with Incident Management, Change Management, and Business Continuity Security Organisation includes establishing a global security services team tasked with managing operational
Penetration Testing
Application Servers
Our web application is tested by a reputable 3rd party organisation at least annually, and the results of the test are available (redacted) by request.
Recommendations are analyzed and if found to be ‘not by design’, Product Backlog Items are raised in our agile development backlog for implementation of fixes.
Our SSO via Identity Server functionality is included in this test. An external infrastructure assessment of our corporate perimeter is tested with HTTP/HTTPS/VPN
Corporate Networks
Our corporate internal infrastructure is tested annually. This currently covers physical hosts, virtual machines and workstation clients. Flaws highlighted by the test are appraised and rectified by our internal technical services team.
High-Level Infrastructure Configuration
Configuration
Evotix currently deploys the following service configurations:
.png?width=500&name=MicrosoftTeams-image%20(13).png)
Our site only allows HTTPS (TLS1.2) traffic to our Load Balancer for application service requests. Multiple web servers deliver the Assure application, which is an ASP.NET MVC web application running in IIS 10. We also host the WCF Assure API on the web servers.
The database server is in High Availability mode. This means that data can never be lost as there are two databases with the other database getting updates from the primary constantly.
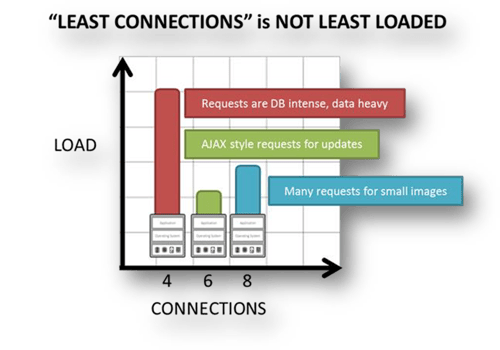
A load balancer serves requests to our application servers and is configured for a least connections operation. Sessions are redirected to the same node (i.e., the sessions are sticky). Only SSL traffic is allowed.
Future Considerations
We are always looking at alternative security enhancements to ensure the robustness of our system and our customers' data. Best practice and continuous improvement in our information security regimen is driven by our ICO registered DPO.
Backups
Assure uses AWS automatic snapshot technology which ensures restoration can quickly occur.
When it comes to our database backups, we can restore the database within 5 minutes prior to failure.
System APIs
Assure employs several APIs for consuming data into registers. These are:
- Equipment Maintenance
- Equipment
- Personnel
- Supplier Register
- Training Course
- Training
- Vehicle Register
It should be stressed that the provided APIs are for the sole purpose of connecting to customer systems and consuming specific information to allow speedy population of static registers in the Assure solution.
Our implemented APIs do not allow full communication or integration between Assure and customer systems to perform any functions other than consume data to populate registers.
In-Transit Security
The Assure website is protected by endpoint SSL encryption.
We use an Amazon certificate. Our signature algorithm is SHA256RSA, employing a SHA256 signature hash algorithm with a 2048-bit RSA public key.
We employ forms-based authentication via TLS 1.2, AES 256 GCM (Galois/Counter Mode: symmetric key cryptography block cyphers) with ECDHE (elliptic curve diffie-hellman key exchange) signed with RSA keys.
Data In-Transit Outside Assure
If a requirement exists for the customer to pass information to Evotix (for example, to populate tables during configuration) which may contain commercially sensitive information or information that would be subject to data protection, Evotix will provide instructions to complete secure transfer of that data using our bespoke TLS secured GateKeeper application.
Data At-Rest
All data stored in the Assure service is encrypted at rest using industry standard AES-256 encryption. This includes data on web/app servers, databases (including associated snapshots and backup) and attachment storage.
Data Protection
We are registered as a data controller with the UK Information Commissioner's Office. Our data protection registration number is Z5414699.
We have voluntarily appointed a Data Protection Officer in pursuit of best practice arrangements for compliance, transparency and clear accountability driven by a role that directly reports to the highest management level in the organisation.
Evotix has put in place appropriate technical and organisational measures that includes physical, electronic and managerial procedures to prevent unauthorized access to your personal data, maintain personal data accuracy, ensure correct use of information, and secure any personal data we collect online. We are accredited to ISO27001 and are Cyber Essentials certified.
Data Protection
As a Software as a Service provider, any data which you add to Assure would remain yours as the Data Controller. We only act as the Data Processor.
In line with the technical and organisational measures outlined above, we fully comply with GDPR including:
- The ability to restrict the geographies within which your data will be processed
- Assure and our Technical Support desk supporting you in serving Data Subject Access Requests
Accreditation
Evotix is Certified to ISO 9001, ISO 27001 and is Cyber Essentials assessed.